Spyware Protection
- Home
- Spyware Protection
What is Spyware?
Spyware is a stealthy type of malware that secretly monitors or tracks your digital activities, often capturing sensitive information such as passwords, financial data, or browsing habits without your consent.
Unlike ransomware, the malware that demands money, or trojans, which install backdoors in your device, spyware itself is just quietly gathering personally identifying information from you, which goes to cybercriminals or unscrupulous advertisers. The data that it can pull can range from login to keyboard inputs or online purchases and can result in identity theft, fraud, or complete privacy violation.
Today's spyware are extremely sophisticated and often come packaged in free software, browser extensions, or through infected sites. Many variations can employ various camouflage techniques that may allude detest conventional security or anti-virus solutions by masquerading as something like any other legitimate app or normal system processes.
.webp)
Different Types of Spyware:
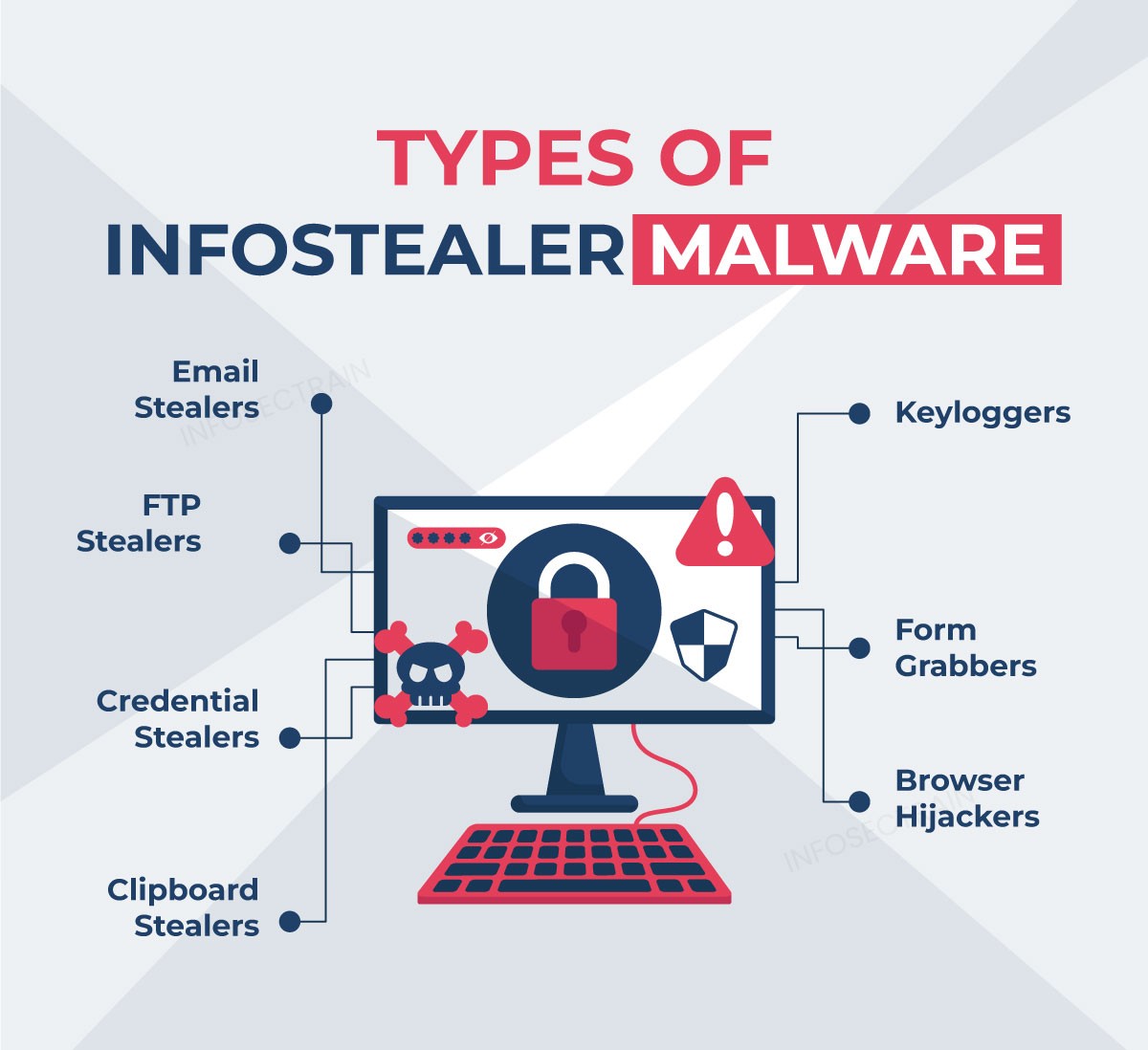
- Infostealers: Capture login credentials, banking details, and other personal data from browsers or installed applications.
- Keyloggers: Capture and store every keystroke you make on your keyboard, including usernames, passwords, and private messages.
- Browser Hijackers: Alters your browser settings so that you're redirected to malicious pages or unwanted advertisements are injected into the page.
- Tracking Cookies: Track your activities on a variety of sites to build a profile of your behaviors in the interest of advertising or worse.
- Mobile Spyware: A very dangerous type of spyware that targets smartphones and allows the hacker to overhear calls, read SMS, and even record the sounds through the phone's microphone and images through the camera.
Popular Spyware Examples:
- Formbook / AZORult (Infostealers): Known as the classic browser data grabber with credential theft and injects evil code into processes.
- FinFisher (Government Spyware): An advanced commercial-grade spyware used by state institutions to surveil their targets.
- CoolWebSearch (Browser Hijacker): Redirects your searches to shady portals or injects ads into web pages.
- FlexiSPY (Mobile Spy): A phone application capable of live comprehensive surveillance of all calls and text messages in addition to precise location tracking.
How Spyware Infects You:
- Free Software Bundles: Downloads that sound legitimate, however, include tricky hidden spyware components in the background.
- Malicious Websites: Exploit weaknesses in browsers or trick into installing plugins/updates with spyware on them.
- Phishing Emails: Attachments presented as important documents that execute spyware once opened.
- Drive-by Downloads: Downloads occurring from compromised sites automatically if a user has out of date or vulnerable software.
How Spyware works:
- Stealthy Installation: Many times, these install without user knowledge and make modifications to registry entries or system files for stealth.
- Continuous Monitoring: Usually runs in the background to capture keystrokes, screen activity, or browser data - all the time.
- Data Theft: Quietly sending the information it has collected to a remote server or a marketplace for cybercriminals.
- Persistent Survival: Often is capable of reinstating itself after any attempt is made to clean it, i.e., survived through morphing into different processes and files.
Consequences:
- Stolen identities or drained bank accounts
- Unauthorized monitoring of personal or professional devices
- Extreme invasion of privacy, exposing sensitive chats, emails, or media.
- Manipulation of browser settings that can lead to inadvertent navigation to some potentially malicious sites.
How OmniDefender Protects You:
- Advanced Spyware Engine: Engine-Expertly recognizes hidden processes, registry changes, and data-harvesting scripts.
- Real-Time Keylogger Detection: Detects unusual keystroke recording activity, stopping keyloggers in their tracks.
- Safe Browsing Module: Alerts you in case any site is recognized as an accomplice in distributing spyware or malicious add-ons.
- In-Depth Removal Tools: Thoroughly wipes all infected spyware files and associated registry entries so they can never install again.
Advanced Spyware Defense System
Proactive Monitoring
Do not blindly download "free" things or use third-party installers unless verified to be safe because most of them carry spyware bundles.
Encrypted Backup
Update the operating system and applications frequently in order to fix holes that spyware exploits.
AI-Driven Heuristics
Employs an intelligent engine to spot new or morphing spyware strains that traditional signature-based scanning might miss.
Privacy Shield
Provides optional keyboard encryption, camera/microphone usage alerts, and other controls to limit spying avenues.
How to Protect Yourself from Spyware Attacks
Essential Security Practices:
- Download Caution: Do not download "free" things or use third-party installers unless verified to be safe because most of them carry spyware bundles.
- Frequent Updates: Update the operating system and applications frequently in order to fix holes that spyware exploits.
- Browser Hygiene: Use only trusted browser extensions and eliminate any plugins that are not necessary. Get rid of cookies frequently.
- Strong Credentials: Lay up strong passwords, multi-factors, and never reuse any passwords long gone.
Advanced Protection Measures:
- Behavior Blockers: OmniDefender's core behavior analysis can perform automatic blocking of any suspicious processes.
- DNS Filtering: Prevent incidental navigation to known malicious domains associated with spyware networks.
- Encrypted Communication: Minimize the collection of intelligence on your device contacts through the use of a VPN or encrypted messaging tools.
- Regular Security Audits: Provide periodic checks for unknown applications or processes running on the device.
Emergency Preparedness:
- Incident Response Plan: Include the procedures for isolating infected devices, changing passwords, and contacting authorities in the event of suspected identity theft.
- Offline Backups: Have backups that can't be corrupted, encrypted, or demanded for ransom by spyware.
- Emergency Contacts: Maintain a list of whom to call (bank, IT personnel, etc.) in case account credentials or sensitive data have been compromised.
- System Restore Points: Save snapshots or restore images to your critical systems in order to revert the damage caused by spyware in case of a severe imminent threat.
Daily Best Practices:
- Run Scheduled Scans: Now install OmniDefender so that it will automatically scan for hidden spyware installations.
- Limit App Permissions: Do not provide permissions to apps beyond the minimal requirements, especially on mobile devices.
- Privacy Settings: Constantly review privacy settings by browsers, social networks, and OS to minimize data collection.
- Camera & Mic Alerts: Be mindful of any lights or notifications that signal unexpected usage of a device.