Crypto Malware Protection
- Home
- Crypto-Malware
What is Crypto Malware?
Crypto malware (also known as to cryptojacking or malicious coin mining) secretly utilizes your system’s processing power to mine cryptocurrencies like Bitcoin, Monero, or Ethereum, without your consent. This stealthy behavior can drastically reduce performance, increase electricity costs, and even cause hardware damage.
Unlike traditional ransomware that encrypts your files for ransom, crypto malware stays hidden, continuously running in the background as long as possible. The attackers profit directly from your CPU/GPU cycles, effectively stealing your resources to make cryptocurrency.
Advanced crypto malware can also spread laterally through networks, hijack cloud environments, or infect IoT devices— fueling large-scale mining operations that are challenging to detect with conventional antivirus methods.

Different Types of Crypto Malware:
- Browser-Based Cryptojacking: Malicious JavaScript that runs in your browser and mines cryptocurrency as you linger on the compromised page.
- Trojan-Style Miners: Executable malware posing as legitimate software that monopolizes CPU or GPU resources in the background.
- Network-Wide Worms: The crypto malware is self-replicating and spreads across a network to infect multiple endpoints to boost its mining abilities.
- Cloud Exploit Miners: Take over under-provisioned cloud instances by quietly deploying containerized miners for larger revenues.
Popular Crypto Malware Examples:
- CoinHive Scripts: JavaScript-based cryptojacking scripts that exploited compromised ad networks or vulnerable websites, thus compromising their pages.
- CryptorBit: Merged classic ransomware capabilities with cryptomining, doubling attackers' profits.
- Norman Miner: A Trojan miner known for infecting machines through phishing campaigns, then spawning stealthy processes.
- XMRig Variants: Popular open-source Monero miners that threat actors incorporate into Trojan downloads or malicious scripts.
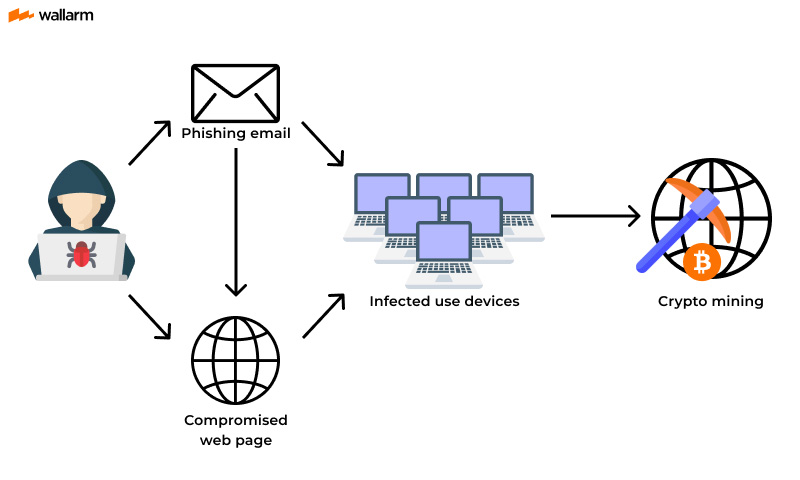
How Crypto Malware Infects You:
- Browser Exploits: Scripts injected into or pop-ups running cryptomining tasks within your active browser tabs.
- Phishing Emails: Malicious attachments or macros that, upon opening, will run a miner executive.
- Software Cracks & Torrents: Pirated software prizing some "free" downloads conveys a hidden cryptominer along with its path.
- Brute-Force Attacks: Weak credentials at a server or IoT devices would permit for infecting cryptominers by attackers.
Consequences:
- System performance suffers drastically and is soaked with power. Overheating, shortened hardware life, or sudden rebooting due to heavy CPU or GPU loads.
- There is a risk of the miner compromising a user's system, which could lead to a larger scale network compromise.
- Potential pivot into more severe network compromises once a miner gains a foothold.
- Financial losses for organizations due to wasted resources and downtime.
How OmniDefender Protects You:
- Real-Time Miner Detection: Keeping tabs on large spikes in CPU/GPU usage quickly flags cryptomining processes.
- Script Blocking: Locates JavaScript-based scripts launching cryptojacking in your browser and stops them from ever turning on.
- Network Scanning: Detects suspicious IPs or pool addresses known for cryptomining traffic.
- System Hardening: Guards against exploit vectors by patching vulnerabilities and limiting installations of unauthorized software.
Advanced Crypto Malware Defense System
Behavior Analysis
Continuously inspects running processes for cryptomining signatures, suspicious memory usage, and CPU overdrive patterns.
Resource Monitoring
Tracks baseline system performance and alerts you to sudden spikes in CPU/GPU usage that could indicate hidden miners.
AI-Driven Heuristics
Identifies new cryptomining variants by analyzing suspicious network connections and resource usage anomalies.
Automated Quarantine
Instantly isolates miners, terminates malicious processes, and blocks known mining pool addresses to prevent further exploitation.
How to Protect Yourself from Crypto Malware
Essential Security Practices:
- Constant Updates: Ensure operating system, drivers, and applications are regularly updated to prevent known vulnerabilities from being exploited for mining.
- Secure Browsing: Use content blockers or NoScript to avoid crypto-mining ads.
- Email Vigilance: Do not open attachments from unknown people or enable macros across any Strange documents.
- Strong Passwords: Plan for two-factor authentication to protect cloud servers and other critical systems against brute-force.
Advanced Protection Measures:
- Network Segmentation: As far as possible, host critical assets separately to prevent lateral spread if a cryptojacker breaks in.
- Traffic Inspection: Inspect outgoing connections for suspicious pool addresses or high uploads.
- Least Privilege Model: Assign minimum rights to applications. That way, compromise of the applications will not bear a hard impact.
- Threat Intelligence: For continued knowledge of new cryptojacking techniques, IoCs, and compromised domains, always be updated.
Emergency Preparedness:
- Incident Response Plan: Identify and act on disconnection of infected machines and removal of miner-serving scripts in order to restore normal operations.
- Offline Backups: Regularly back up critical systems and networks for speedy recovery in case the miner impairs the normal function of your environment.
- Emergency Contacts: Have immediate access to security experts or, warranting some IT action, people who can work in the context of crypto malware for fast remediation.
- Forensic Tools: Prepare analytical tools for the memory and disk to gather evidence of miner activities or malicious scripts.
Daily Best Practices:
- Continuous Monitoring: Use OmniDefender to continuously monitor any anomalous CPU/GPU usage in real-time.
- Safe Downloads: Only obtain software from official sources or verified repositories to avoid Trojanized installers.
- Use Ad-Blockers: Reduce the volume of crooks using advertisement services that disseminate cryptojacking javascript.
- Educate Users: This means teaching your team or family members to know the warning signs of cryptojacking.